Over 12,000 KerioControl firewalls exposed to exploited RCE flaw

Over twelve thousand GFI KerioControl firewall instances are exposed to a critical remote code execution vulnerability tracked as CVE-2024-52875.
KerioControl is a network security suite that small and medium-sized businesses use for VPNs, bandwidth management, reporting and monitoring, traffic filtering, AV protection, and intrusion prevention.
The flaw in question was discovered in mid-December by security researcher Egidio Romano (EgiX), who demonstrated the potential for dangerous 1-click RCE attacks.
GFI Software released a security update for the problem with version 9.4.5 Patch 1 on December 19, 2024, yet three weeks later, according to Censys, over 23,800 instances remained vulnerable.
Early last month, Greynoise revealed it had detected active exploitation attempts leveraging Romano’s proof-of-concept (PoC) exploit, aimed at stealing admin CSRF tokens.
Despite the warning about active exploitation, threat monitoring service The Shadowserver Foundation now reports seeing 12,229 KerioControl firewalls exposed to attacks leveraging CVE-2024-52875.
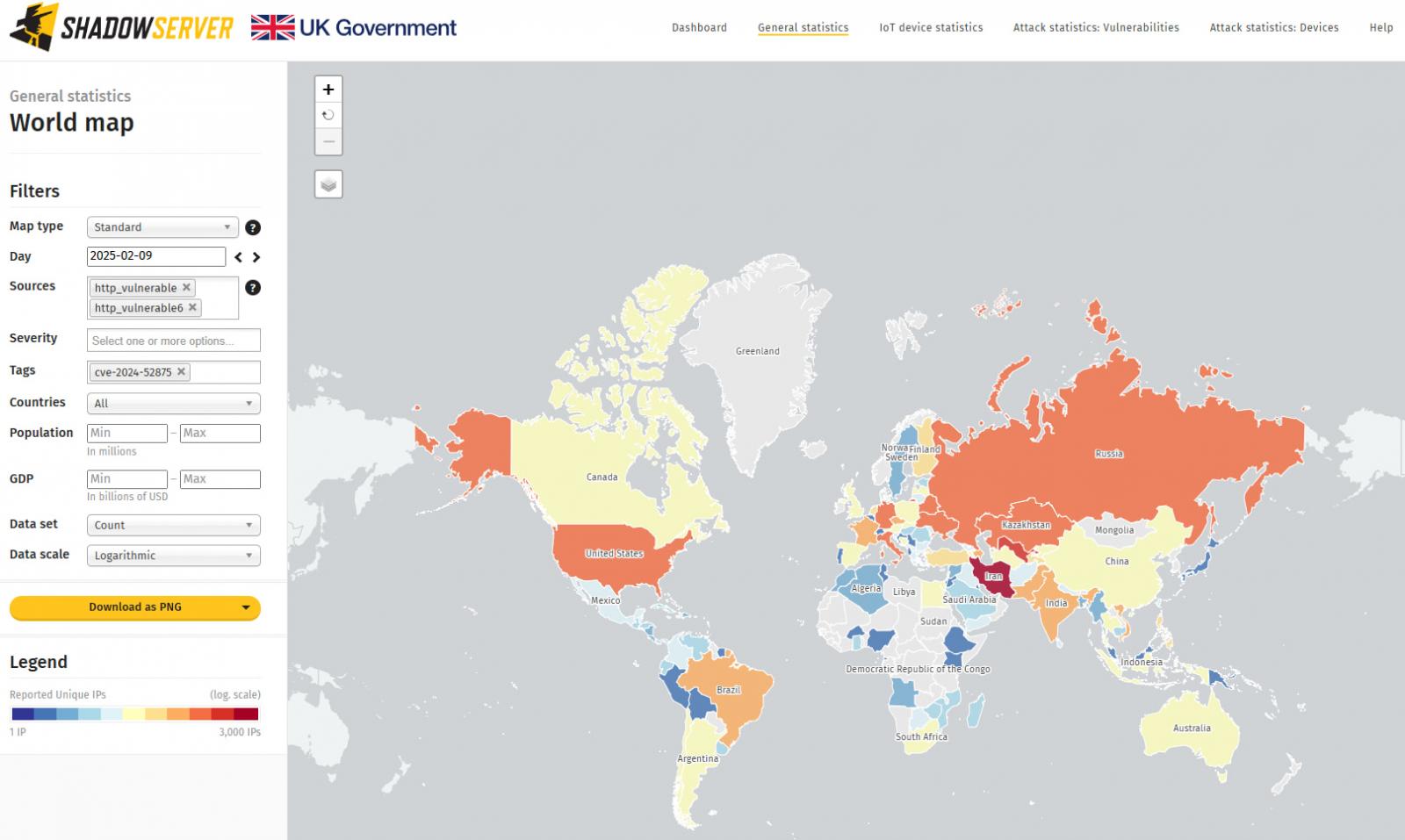
Source: The Shadowserver Foundation
Most of these instances are located in Iran, the United States, Italy, Germany, Russia, Kazakhstan, Uzbekistan, France, Brazil, and India.
With the existence of a public PoC for CVE-2024-52875, the requirements for exploitation are low, allowing even unskilled hackers to join the malicious activity.
“User input passed to these pages via the “dest” GET parameter is not properly sanitized before being used to generate a “Location” HTTP header in a 302 HTTP response,” explains Egidio Romano.
“Specifically, the application does not correctly filter/remove linefeed (LF) characters. This can be exploited to perform HTTP Response Splitting attacks, which in turn might allow to carry out Reflected Cross-Site Scripting (XSS) and possibly other attacks.”
“NOTE: the Reflected XSS vector might be abused to perform 1-click Remote Code Execution (RCE) attacks.”
If you haven’t applied the security update yet, it is strongly advised that you install KerioControl version 9.4.5 Patch 2, released on January 31, 2025, which contains additional security enhancements.
Source link











